What is Sysjoker :
Sysjoker is a malicious backdoor software that was first discovered by Intezer in December 2021. It is advanced and written in C++. Sysjoker is a multi-platform malware that targets Windows, Linux, and macOS operating systems. Common methods of attack for Sysjoker include email attachments, malicious advertisements, and infected software. The Sysjoker malware poses a significant threat as it can be used for sophisticated attacks. These attacks can involve ransomware, crypto miner installation, or spyware.
Behavioural analysis :
Once Sysjoker infects a machine, it will start performing the following actions:
- Creating folders and files
- Establishing its presence
- Carrying out procedures for the discovery of other systems
- Hide in standby mode, waiting for commands.
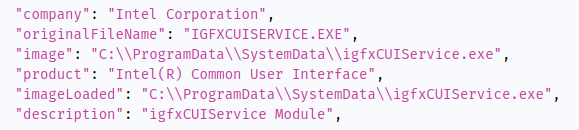
On all platforms, after running Sysjoker, it will create certain directories and disguise itself as a system update. On Windows, it disguises itself as a well-known Intel Common User Interface process, igfxCUIService.exe.
Sysjoker will try to stabilize itself by various means depending on the operating system:
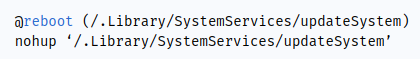
Linux/Unix : Runs a cron process and executes the nohup command.
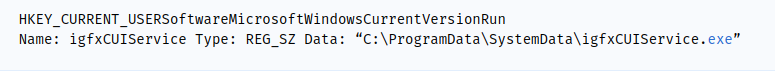
Windows : It is added to the list of Windows executables.
macOS : Creates a file in the LaunchAgents folder.
![]()
Then, Sysjoker will execute Living off the Land (LOtL) commands to gather network and system information about the infected machine. It uses temporary text files on Windows machines to log the results of LOtL and C2 commands. After all these actions, the infected machine is ready to receive commands from the C2 server.
Malicious files (HASH):
Then, Sysjoker will execute Living off the Land (LOtL) commands to gather network and system information about the infected machine. It uses temporary text files on Windows machines to log the results of LOtL and C2 commands. After completing these actions, the infected machine is prepared to receive commands from the C2 server.
Linux:
bd0141e88a0d56b508bc52db4dab68a49b6027a486e4d9514ec0db006fe71eed
d028e64bf4ec97dfd655ccd1157a5b96515d461a710231ac8a529d7bdb936ff3
Windows:
1ffd6559d21470c40dcf9236da51e5823d7ad58c93502279871c3fe7718c901c
61df74731fbe1eafb2eb987f20e5226962eeceef010164e41ea6c4494a4010fc
649a97980ed3eeed9a9b61eafd1d60c8d2d15c3be1d6acd3723af87fbda2e8fd
macOS:
1a9a5c797777f37463b44de2b49a7f95abca786db3977dcdac0f79da739c08ac
fe99db3268e058e1204aff679e0726dc77fd45d06757a5fda9eafc6a28cfb8df
d0febda3a3d2d68b0374c26784198dc4309dbe4a8978e44bb7584fd832c325f0
e83f6fdf04928cf1be0cec6c4c5a583561a06b5c18b559dc2298ae174709bf68
C2 domains :
These are the domains where the malware sends DNS requests and receives C2 commands:

Files and directories created after infection:
The following are the files and directories created by Sysjoker after it infects a computer:
Linux:
/.Library/
/.Library/SystemServices/updateSystem
/.Library/SystemNetwork
/.Library/log.txt
Windows:
C:\ProgramData\SystemData
C:\ProgramData\SystemData\igfxCUIService.exe
C:\ProgramData\SystemData\microsoft_Windows.dll
Several temporary files in the C:\ProgramData\SystemData directory
macOS:
/Library/MacOsServices
/Library/MacOsServices/updateMacOs
/Library/SystemNetwork
/Library/LaunchAgents/com.apple.update.plist
Locating Sysjoker:
Cyber Radar provides detection rules that will generate alerts when Sysjoker is detected on a machine.
Windows :
Cyber Radar logs events using sysmon
The System Monitor (Sysmon) is a Windows system service that monitors and records system activity in the Windows event log file. The capabilities of Sysmon include:
1) Detects files when they are created, deleted or changed and records the hashes of the files using SHA1 , MD5, SHA256 or IMPHASH.
2) Detects network connections and DNS queries
3) Logs when a new process is created or a process is terminated.
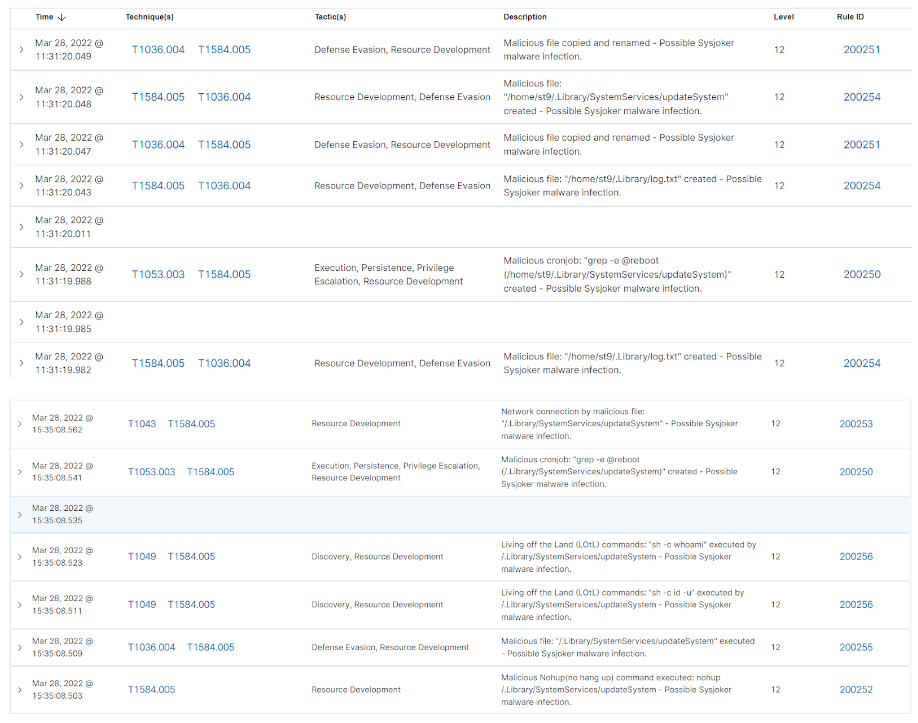
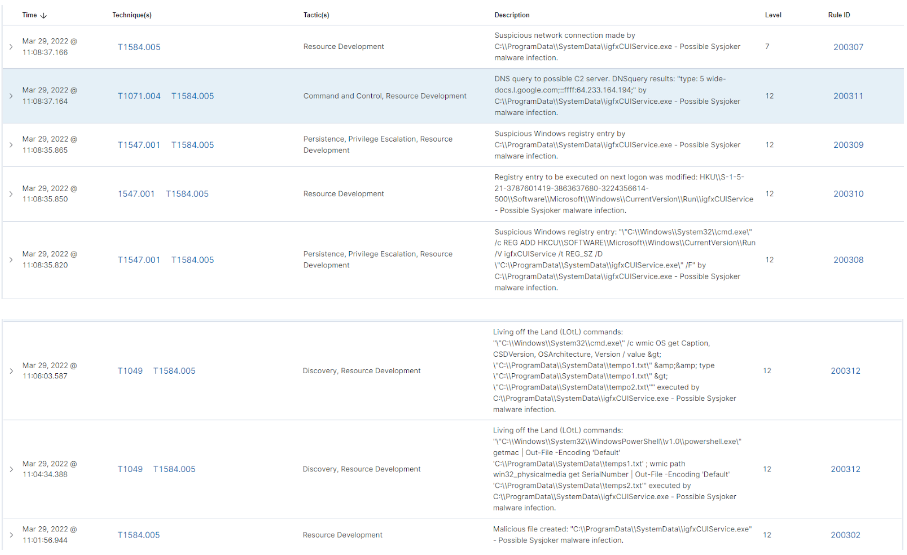
The image below shows some notifications about Sysjoker :
Linux /Unix :
To detect Sysjoker on Linux/Unix machines, Cyber Radar uses the following methods:
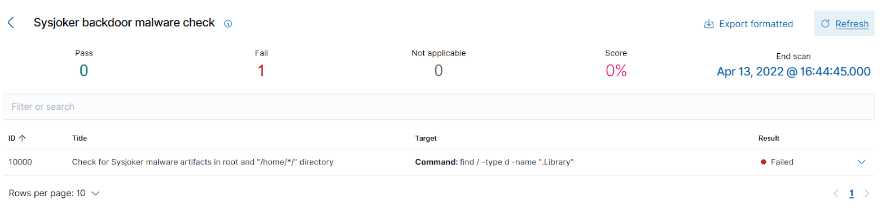
- SCA (Security Configuration Assessment): Cyber Radar SCA (Security Configuration Assessment) can be used to monitor system hardening and configuration policies and find ways to resolve any issues. We utilize SCA policy to scan the folder created after running Sysjoker.
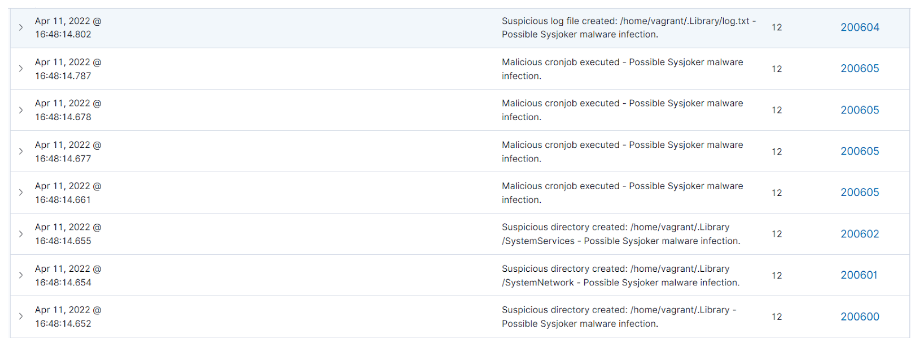
- Auditd: Auditd is a framework that can be used for event monitoring on Linux/Unix systems. It can be utilized to monitor the folders and files created by Sysjoker. Additionally, we use Auditd to identify the cron job executed by Sysjoker.
- SysmonForLinux: SysmonForLinux provides enhanced event monitoring capabilities, such as process monitoring, network connections, and file system changes. These events are then monitored by Cyber Radar, and if any suspicious activity related to Sysjoker is detected, the corresponding notification will be displayed.