We provide basic testing to evaluate the percentage of your users/employees who are susceptible to phishing attacks. This is achieved through simulating phishing attacks, also known as social engineering.

Basic Tests
"We phish" your employees for a good cause.
We offer fully automated phishing simulations with thousands of multi-purpose templates and various themes from the phishing community, including fake banking websites.
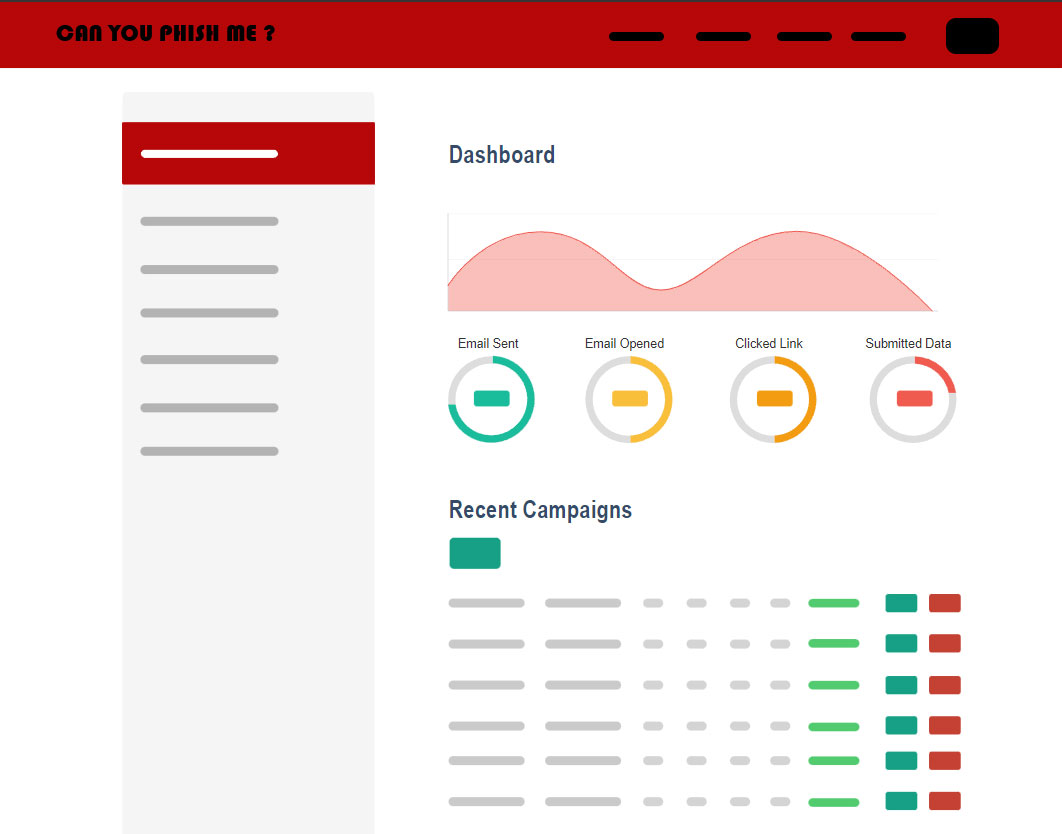
Results and reports are provided on a weekly basis.
Reports are provided on a weekly basis, indicating the extent to which your company's executives are properly trained. These reports include statistical data and graphs related to both security awareness and phishing.
PLATFORM FEATURES
Smart Groups
Με την πανίσχυρη νέα λειτουργία τα Smart Groups, χρησιμοποιώντας την συμπεριφορά κάθε υπαλλήλου και τα χαρακτηρίστηκα του χρήστη ώστε να προσαρμόσετε όπως εσείς θέλετε τα phishing campaigns, training assignments, remedial learning και τα reporting’s.
Customized Phishing Pages
In addition to the provided templates, we can customize scenarios based on personal information, creating targeted spear phishing campaigns. Each phishing template can have its own customized page and specifically capture sensitive information from the phishing attempt.
Customized Attachments
The customized Phishing Templates we have can include simulated attachments in the following formats: Word, Excel, PowerPoint, and PDF (as well as zipped versions of files).
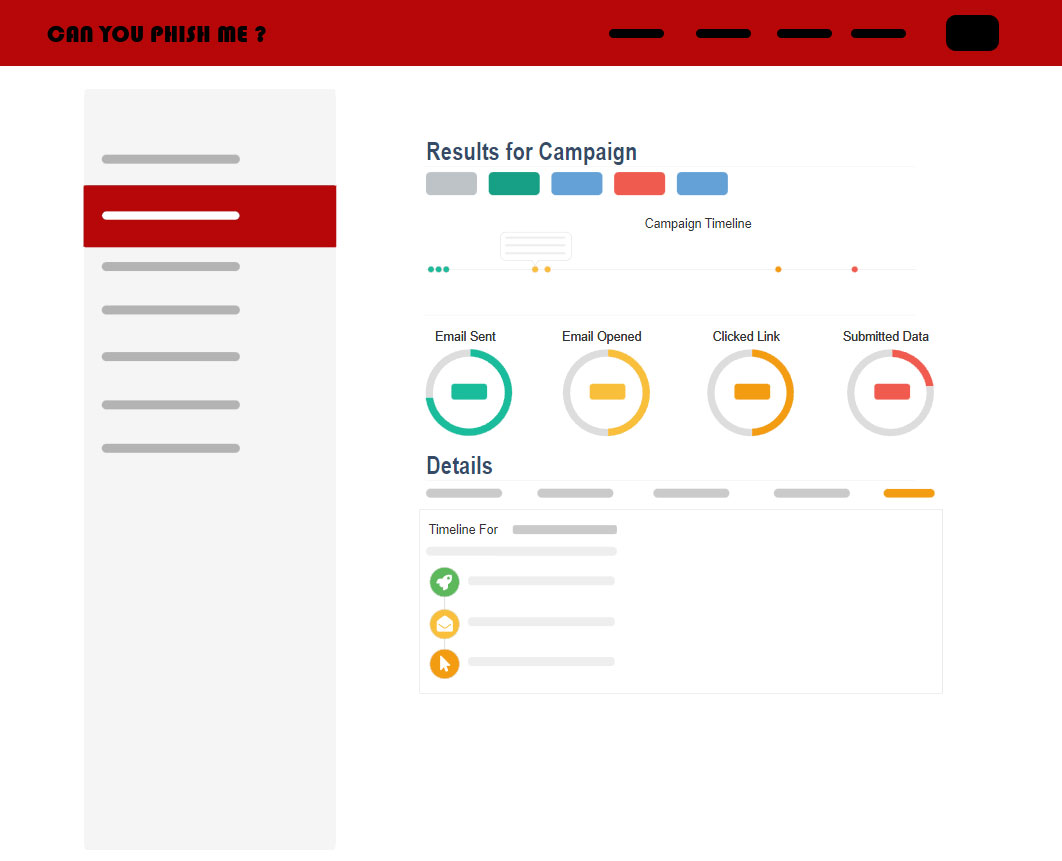
Advanced Reporting
You'll be able to see reports from training and phishing campaigns, and even an overview of the last 5 campaigns. With over 50+ built-in reports, information is also obtained that provides a holistic view of your entire organization with very detailed reporting on key awareness training indicators.
Your own comprehensive Security Awareness Training Program
Περισσότερο από ποτέ, η έλλειψη γνώσεων των στελεχών σας είναι ο αδύναμος κρίκος του network security της εταιρίας σας. Θα πρέπει να εκπαιδευτούν προσεκτικά ώστε μετά την εκπαίδευση να είναι έτοιμοι και να έχουν στο μυαλό τους πάντα και πρώτα από όλα το security.
CAN YOU PHISH ME is the first Security Awareness platform in Greece with over 1,000 phishing techniques ready to train you!
Η πλατφόρμας μας, σας προσφέρει self-service σύνδεση και δοκιμές phishing πριν αλλά και μετά την εκπαίδευση που σας δείχνουν το ποσοστό των τελικών χρηστών όπου είναι επιρρεπείς στις επιθέσεις phishing.
Measure the security awareness of users and measure the culture posture of your organisation.
These two scientific evaluations help you to adapt the training to address gaps and weaknesses, and to monitor the impact of your safety awareness training programme and to improve your users' knowledge and sense of safety awareness over time.
See first hand if your organization or company can pass and collect the 7 levels of security and the 7 dimensions of security culture from your baseline assessment and research and even track the continuous improvement of your organization.
With our innovative end-user security awareness training interface, your users will have access to ongoing and new training materials to help them evaluate any social engineering attack that happens to your company.
With our platform, your users will be entitled 24/7 to defined training that will facilitate learning anytime and anywhere they are.
Do you want to complement your security awareness training content with your organization's customized training or other corporate training content?
Τώρα μπορείτε! Ανεβάζουμε το δικό σας βίντεο και το διαχειριζόμαστε μαζί με το εκπαιδευτικό σας περιεχόμενο όλα σε ένα μέρος.
Too many IT professionals don't know exactly where to start when it comes to creating a security awareness program that works for their organization.
Our platform allows you to create a customized program for your organization that helps you implement all the steps to run a complete Security Awareness Training Program in just a few minutes.


Phishing
We can schedule regular tests on the Phishing Security Tests (PST) which has more than 1000 templates. We can also create your own custom phishing templates.
Our Phishing Reply service allows you to track whether a user replies to a simulated phishing email and can record the information sent in the reply.
You can also track the links selected by users, as well as control and monitor whether users open Office attachments and then trigger macros.
If an employee falls victim to one of these simulated phishing attacks, you have many options for remediation, including immediate remedial online training. We can schedule one-time, weekly, bi-weekly or monthly simulated phishing attacks and immediately see which employees fall victim to these social engineering attacks.
Enterprise-strength Reporting
Θα λαμβάνετε αναφορές με τις λειτουργίες Advanced Reporting που θα σας παρέχουν μετρήσεις που μπορούν να χρησιμοποιηθούν για το security awareness σε θέματα ασφάλειας.
Executives gain the insight they need to maximise the return on their safety awareness training and monitor safety compliance. The administrator console provides instant graphs of training effectiveness.
Social engineering (Social engineering)
Definition
Social engineering is the act of verbally manipulating people in order to extract information.
Although similar to trickery or simple fraud, the term is mainly associated with deceiving individuals in order to obtain confidential information necessary to access a computer system.
Usually the practitioner never comes face to face with the person who is cheating or deceiving. Although the term may not be accurate or successful it is now well established.
How it works
It relies mainly on human curiosity or greed and ignorance. Many people think that a good antiviral protects them but these only work for widely known viruses and for widely known techniques and not for a specially made "virus". Many also, either out of credulity or out of politeness, will not refuse to give evidence to someone who asks politely or under supposed 'pressure'.
Ο άμεσος στόχος δεν είναι πάντα η αποκάλυψη του κωδικού. Για κάποιον που θέλει να διεισδύσει σε ένα υπολογιστικό σύστημα πολλές φορές είναι αρκετή ακόμα και η απλή γνώση του αριθμού έκδοσης του λειτουργικού συστήματος ή άλλων προγραμμάτων που χρησιμοποιεί ο χρήστης. Με αυτές τις πληροφορίες μπορεί να μάθει αν υπάρχουν “τρύπες” στα προγράμματα και να τις αξιοποιήσει. Άλλες πληροφορίες που μπορεί να συλλέξει κάποιος, και που πιθανά να είναι χρήσιμες, όπως οι ημερομηνίες γέννησης, τα ονόματα των παιδιών, τα ονόματα υπευθύνων για τη μηχανογράφηση κ.α. συλλέγονται είτε μέσω συνομιλίας είτε από τα λεγόμενα κοινωνικά δίκτυα είτε από τις ιστοσελίδες της εταιρείας.
This information is later used in conversation, whether by phone, email or instant messaging, to convince the victim that he or she is an acquaintance and thus extract even more information or, even better, a password.
OUR TARGET
Στόχος μας είναι η εκπαίδευση του προσωπικού μιας επιχείρησης ή ενός εργονανισμού μέσω πλατφόρμας εκπαίδευσης, παρακολούθησης και ελέγχου απόδοσης των εκπαιδευομένων, η οποία υποστηρίζει ένα ευρύ φάσμα εκπαιδευτικών προγραμμάτων ασφαλείας.
The main topics covered by the training platform include, among others:
1. Credit Card Security
2. Create & Manage Strong Passwords
3. Secure Management of Sensitive Data
4. Safe Navigation
5. Safe use of Social Media
6. Corporate Email Breach Attacks (BEC Scams)
7. Ransomware attacks
8. E-mail Spoofing attacks
9. Malware Attacks
10. Phishing attacks
11. USB attacks
12. Social Engineering
13. Data Classification (Data Classification)
14. Creating a "Human Firewall" (Human Firewall)
15. User Recognition and Identification
16. Safety When Using Mobile Devices
17. Safe Internet Behaviour
18. Call Center & Help Desk Awareness (Call Center & Help Desk Awareness)
19. Raising awareness of the Top Safety Issues
20. Raising the awareness of Managers on issues of Computer Security & Data Protection
21. Safety in the Work Environment
22. Understanding Encryption
As secure as our company's operating systems are, e.g. firewalls, antivirus, etc., the weakest link is the human factor where the wrong click can cause a lot of damage.
Επικοινωνήστε μαζί μας σχετικά με τις υπηρεσίες και τα προϊόντα μας και θα σας καθοδηγήσουμε στην καλύτερη λύση!
