Αναβαθμίζουμε την ασφάλεια των πελατών μας!
Τι είναι το Vidar Infostealer :
Vidar infostealer is a malware that steals sensitive information from cryptocurrency wallets, web browsers and other applications such as WinSCP, Telegram and Authy 2FA on infected Windows systems. It can collect stored credentials, hardware and software information on infected systems. The malware sends the stolen data to a remote control and command (C2) server.
Στο παρελθόν, το Vidar επικοινωνούσε με διακομιστές C2 που ήταν κωδικοποιημένοι μέσα στο κακόβουλο λογισμικό. Πρόσφατα, το κακόβουλο λογισμικό επικοινωνεί με διακομιστές C2 που αλλάζουν συνεχώς και τα λαμβάνει από νόμιμες ιστοσελίδες.
Malicious users usually distribute Vidar by sending fake emails, cracked versions of commercial applications and keygens. Recently, malicious users have misused AnyDesk and Notepad++(cracked versions) to distribute this malware.
Behavioral analysis:
When Vidar infostealer is run on a system, it performs the following behaviors:
- Vidar downloads freebl3.dll, mozglue.dll, msvcp140.dll, nss3.dll, softokn3.dll and vcruntime140.dll from a C2 server and stores them in the C:\ProgramData folder of the infected system. Vidar uses these DLL files to steal information from the infected system.
- The malware creates a folder C:\ProgramData\files . This folder contains subfolders and files that store the stolen data from the infected system.
- Vidar archives the stolen data in a C:\ProgramData.zip file and sends it to a C2 server.ss
- The malware creates a folder C:\ProgramData\files . This folder contains subfolders and files that store the stolen data from the infected system.
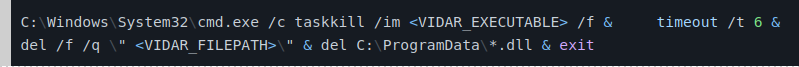
Εντοπισμός του Vidar infostealer:
Cyber Radar has two techniques for detecting Vidar infostealer as follows:
Windows event logging and evaluation: Cyber Radar has the ability to detect these actions mentioned above when they occur on a system and when they are detected the corresponding alert is generated in the Dashboard. The alerts are analyzed and evaluated and then the necessary actions are taken to address the incident.
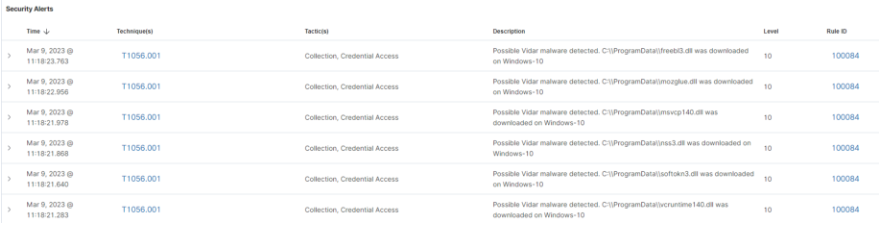
(Εικόνα 1 : Malicious DLL files downloaded)
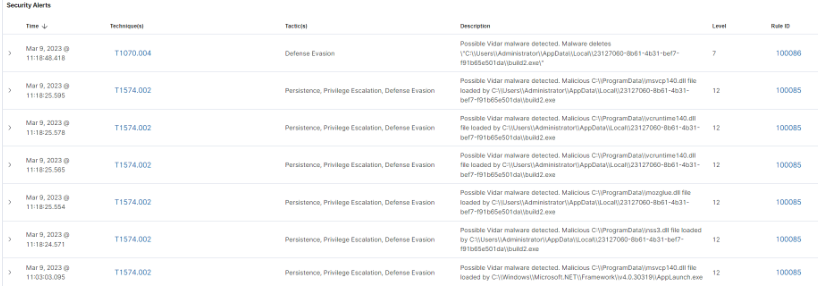
(Εικόνα 2: Malicious DLL files loaded by Vidar, and Vidar deleted a malicious process)
File Integrity Monitoring (FIM): It detects files when they are created, deleted or changed and records the hash of the files using SHA1, MD5, SHA256 and IMPHASH. It then compares the hash of all files with our database (Threat Intelligence) and if any hash matches that of Pandora the corresponding alert will be generated in the Cyber Radar Dashboard and immediately deleted automatically.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

