It is known that malware utilizes the services of the Windows operating system to achieve the attacker's desired objectives.
Για παράδειγμα, μια υπηρεσία του λειτουργικού συστήματος των Windows, όπως το Vssadmin, μπορεί να χρησιμοποιηθεί από ransomware για να εμποδίσει τη δυνατότητα επαναφοράς του συστήματος από τα αντίγραφα ασφαλείας (backup) σε ένα μηχάνημα Windows. Το Vssadmin είναι μια εντολή του συστήματος που διαχειρίζεται την υπηρεσία Volume Shadow Copy Service (VSS) που χρησιμοποιείται για τη δημιουργία αντιγράφων ασφαλείας του συστήματος.
Με την χρήση του Vssadmin, το ransomware μπορεί να διαγράψει ή να απενεργοποιήσει τα αντίγραφα ασφαλείας του συστήματος, εμποδίζοντας έτσι τη δυνατότητα επαναφοράς του συστήματος από τα αντίγραφα ασφαλείας σε περίπτωση που τα δεδομένα του χρήστη έχουν κρυπτογραφηθεί από το ransomware.
Αυτό το άρθρο επικεντρώνεται στο πώς το Cyber Radar μπορεί να χρησιμοποιηθεί για να ανιχνεύσει πότε εκτελούνται ορισμένες υπηρεσίες του λειτουργικού συστήματος των Windows σε ένα μηχάνημα. Θα προσπαθήσουμε να ανιχνεύσουμε πότε εκτελούνται τα Nltest, BCDedit, Vssadmin, Attrib και Schtasks στη γραμμή εντολών των Windows(cmd). Αν και η εκτέλεση αυτών των εργαλείων δεν είναι συνήθως κακόβουλη και δεν σημαίνει απαραίτητα ότι υπάρχει μια ενεργή επίθεση.
Πρέπει όμως να παρακολουθούνται, για τους ακόλουθους λόγους:
1) To better analyze and understand the events occurring in the monitored systems, we utilize the process of forensic analysis. Through this process, we can retrieve data and information that will assist us in comprehending and accurately reconstructing these events.
2) To detect actions by malicious users.
Detection of malicious actions:
Cyber Radar detects actions performed on your machine by the Nltest, BCDedit, Vssadmin, Attrib and Schtasks services of the Windows operating system.
Nltest:
Nltest is a command-line utility used in Active Directory environments to query domain controllers and analyze the reliability of domains.
BCDEdit:
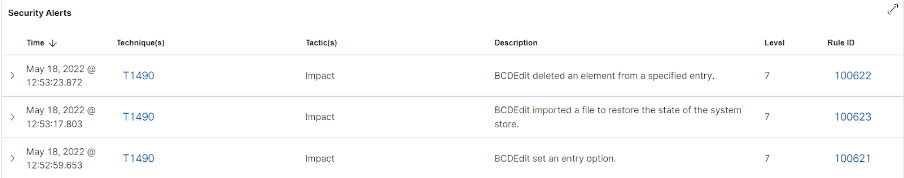
Το BCDEdit είναι ένα εργαλείο που χρησιμοποιείται για την επεξεργασία των ρυθμίσεων εκκίνησης των συστημάτων των Windows. Η Microsoft αναφέρει ότι η εκτέλεση του BCDEdit πιθανόν να είναι ένδειξη δραστηριότητας από ransomware.
Μπορεί να χρησιμοποιηθεί για την “Απενεργοποίηση προειδοποιήσεων και αυτόματων επισκευών μετά από αποτυχίες εκκίνησης που μπορούν να προκληθούν από τη διαδικασία κρυπτογράφησης”. Έχουν δημιουργηθεί κανόνες για την ανίχνευση όταν το BCDEdit κάνει τα ακόλουθα:
1. Sets an input option value.
2. Deletes an item from a record.
3. Imports a file to restore the state of the saved system.
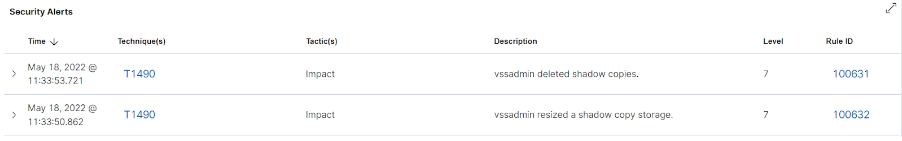
Vssadmin:
Vssadmin is used to manage volume shadow copy backups. Rules have been created to detect deletion and resizing of shadow copy backups.
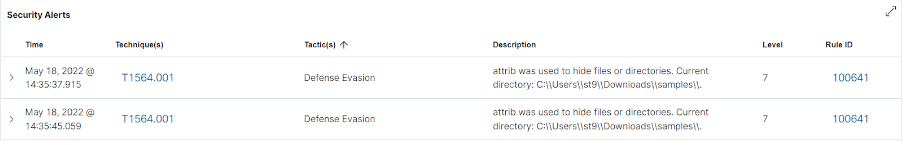
Attrib:
Attrib is a Windows operating system tool used to remove or configure file attributes (hidden, read-only, system, and archive). Attackers use this tool to hide malicious files and folders anywhere on the system.
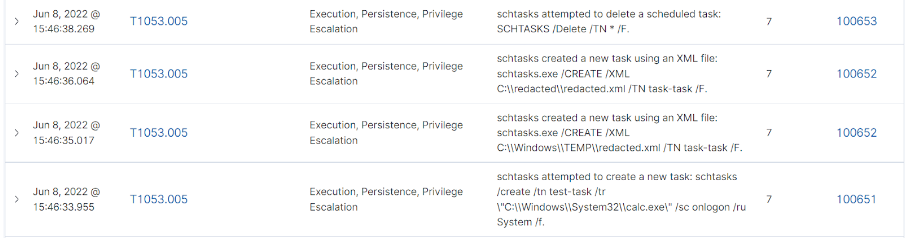
Schtasks:
Το Schtasks είναι ένα εργαλείο που επιτρέπει στους διαχειριστές ενός συστήματος να διαχειρίζονται προγραμματισμένες διεργασίες.
Με το Schtasks μπορούν να δημιουργηθούν, να διαγραφούν, να εκτελεστούν και να τερματιστούν προγραμματισμένες διεργασίες σε ένα τοπικό ή απομακρυσμένο υπολογιστή.
Οι επιτιθέμενοι είναι γνωστό ότι εκμεταλλεύονται αυτό το εργαλείο για τον προγραμματισμό κακόβουλων εργασιών. Υπάρχουν όμως κανόνες, για την ανίχνευση όταν το Schtasks κάνει τα εξής:
1. Creates a new scheduled process.
2. Creates a new scheduled process using an XML file.
3. Deletes a scheduled process.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

