What is Black Basta:
Black Basta is a ransomware that appeared in April 2022 that mainly targets businesses . It has been observed that the ransomware adds the .basta extension to the files that have been encrypted. The common infection attacks of Black Basta are phishing, torrent websites, and adware. The ransomware has two variants which include the Windows variant and the VMWare ESXi variant. The Windows environment variant of the malware targets 32-bit and 64-bit systems of Windows XP, Vista, 7, 10, and 11 versions. After encryption, the wallpaper of the infected machine is changed, and a readme.txt file is added to all folders of the infected machine. The note warns that if the ransom is not paid, the files will be leaked to the cybercriminals' Tor website. The message also contains a link to the Tor website where victims can contact the attackers.
Below are some activities that Black Basta creates during its execution:
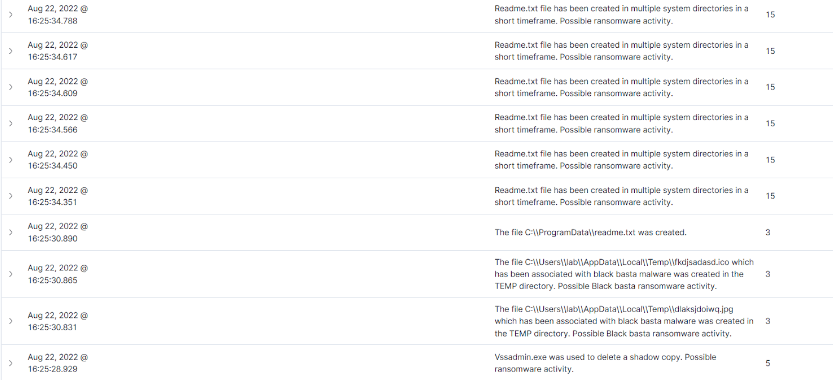
Dropped .ico and .jpg Black Basta files: When running Black Basta, it is observed that the files dlaksjdoiwq.jpg and fkdjsadasd.ico are downloaded to the Appdata\Temp folder of an infected system.
Shadow copy deletion: After execution, the Black Basta malware uses a terminal and executes a command to delete shadow copies on an infected system using vssadmin.exe. Shadow copies, also known as VSS or Volume Snapshot Service, is used to create backups or snapshots of files and storage drives.
Creation of readme.txt files: We also noticed that the Black Basta malware creates a readme.txt file in all directories of the infected computer. The readme.txt file contains a Black Basta message with the URL of a Tor website where victims can interact and negotiate with the attackers.
Defense evasion: Finally, the malware disables the security monitoring agents on the infected computer.
Locating Black Basta:
Cyber Radar has two techniques for detecting Black Basta as follows:
Windows event logging and evaluation: Cyber Radar has the ability to detect these actions mentioned above when they occur on a system and when they are detected the corresponding alert is generated in the Dashboard. The alerts are analyzed and evaluated and then the necessary actions are taken to address the incident.
File Integrity Monitoring (FIM): It detects files when they are created, deleted or changed and records the hash of the files using SHA1, MD5, SHA256 and IMPHASH. It then compares the hash of all files with our database (Threat Intelligence) and if any hash matches that of Pandora the corresponding alert will be generated in the Cyber Radar Dashboard and immediately deleted automatically.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

