What is BlackCat Ransomware:
BlackCat (also known as ALPHV, Noberus) was first detected in November 2021 and is considered one of the most sophisticated and threatening malware types of 2021 and 2022. However, towards the end of 2022 the number of computers infected by BlackCat decreased by 28% compared to previous years.
BlackCat is the first established malware written in the Rust programming language, a new language that is gaining popularity due to its high performance. BlackCat is related to the BlackMatter and DarkSide ransomware variants in terms of source code. The creators of BlackCat advertise the ransomware to interested parties on private forums, such as the darknet XSS, Exploit Forum and RAMP5 forums, where they seek new cybercriminals to join their ranks. Translated with www.DeepL.com/Translator (free version)
This article shows how BlackCat ransomware is detected on Windows devices using Cyber Radar.
Actions that BlackCat ransomware does:
BlackCat is a versatile malware that works via command line and is controlled by humans. It has the ability to use various encryption techniques. Below are some of the important behaviors of the malware:
- BlackCat ransomware uses an access token to execute. The access token is a randomly selected 32-byte token. Below is an example of a command executed by BlackCat
![]()
- BlackCat bypasses User Access Control (UAC) when a user account without administrative privileges runs it. It runs a secondary process under dllhost.exe with the necessary permissions to encrypt a large number of files on a compromised machine.
- BlackCat discovers other devices on the same network by sending a broadcast NetBIOS Name Service (NBNC) message. The malware then uses PsExec to try to infect the servers.
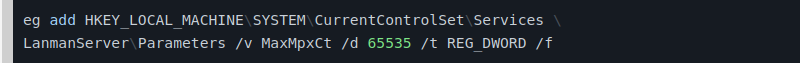
- BlackCat increases the number of pending SMB client requests allowed. Sets the maximum client connection limit to 65535 by modifying the Registry (Windows Registry) to change the MaxMpxCt settings. uses the following command to set MaxMpxCt to 65535:
- BlackCat terminates processes and stops services. For example, it uses the cmd.exe /c "iisreset.exe /stop" command to stop the Internet Information Service on the Server.
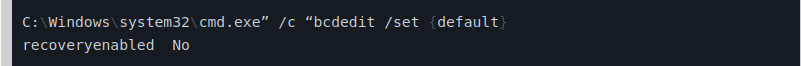
- BlackCat modifies the boot loader to prevent recovery and auto-repair on the Windows machine. It disables the boot recovery function using the following command:
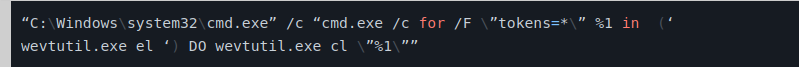
- BlackCat uses wevtutil.exe to clean Windows event logs in order to prevent analysis. It runs the following command to clean up the event logs:
- Disables and deletes the Volume Shadow Copy Service and Hyper-V Volume Shadow Copy Requestor Service. BlackCat uses the wmic.exe command to delete shadow copies on all volumes. It uses the following command:
![]()
Locating BlackCat:
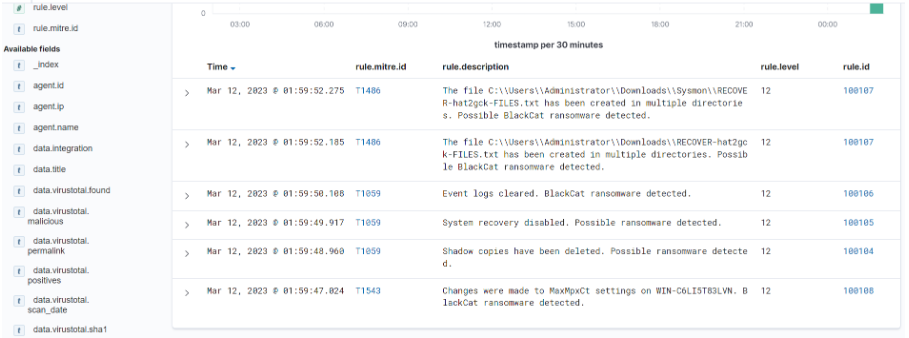
Cyber Radar has two techniques for detecting BlackCat as follows:
File Integrity Monitoring (FIM): It detects files when they are created, deleted or changed and records the hash of the files using SHA1, MD5, SHA256 and IMPHASH. It then compares the hash of all files with our database (Threat Intelligence) and if any hash matches that of Pandora the corresponding alert will be generated in the Cyber Radar Dashboard and immediately deleted automatically.
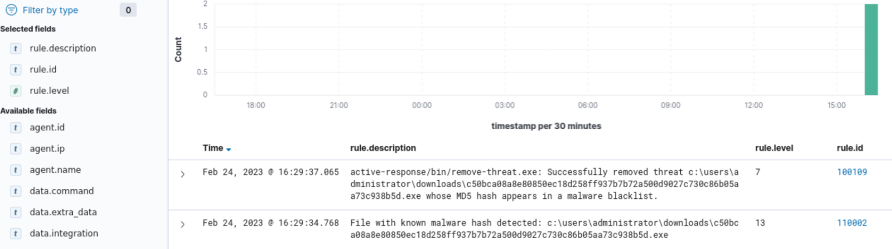
Windows event logging and evaluation: Cyber Radar has the ability to detect these actions mentioned above when they occur on a system and when they are detected the corresponding alert is generated in the Dashboard. The alerts are analyzed and evaluated and then the necessary actions are taken to address the incident.
Μην αφήσετε την ασφάλεια της επιχείρησής σας στην τύχη.
Επικοινωνήστε μαζί μας σήμερα για να δείτε πώς το Cyber Radar μπορεί να προστατεύσει τα δεδομένα και τη φήμη της εταιρείας σας. Μια επένδυση στην ασφάλεια της επιχείρησής σας είναι μια επένδυση για το μέλλον της.
Ανακαλύψτε περισσότερα ή ζητήστε ένα DEMO από εδώ: https://www.audax.gr/gia-epixeiriseis/cyber-radar-unified-xdr-siem-platform/

